SIEM as a service (Cloud)
Cloud SIEM Means Convenience
Put simply, Security Incident Event Management (SIEM) software collects data from the different technologies within your system, monitors and analyzes that data for deviations and possible security risks, and then takes the appropriate action against those threats.
As a system, SIEM was conceived to monitor entire IT networks and keep an eye out for anomalous activity or unusual behaviors, affecting organizations’ internal or external systems.
SIEM systems have been so effective at what they do that organizations of all types have begun implementing them to protect against advanced and persistent threats against their systems, including ransomware, SQL injection attacks, and data breaches.


Why Choose the Cloud
To keep the organization’s information secure and industry compliant a SIEM might be the answer. On-Prem systems keep your data inside the organization but require a relevant amount of investment and manual effort to start up a SIEM solution. SIEM as a Service, particularly when implemented through the cloud, can avoid or reduce these expenses and efforts.
-
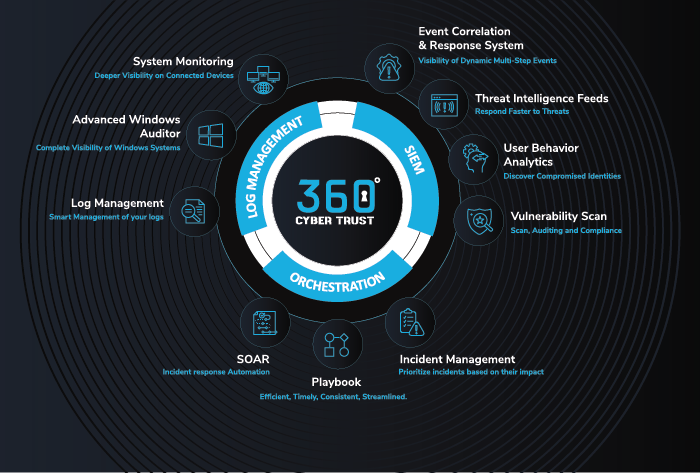
Log Management
Effortlessly collect, analyze, and visualize data in any format from any device with our user-friendly data management solution. Gain valuable insights in real-time or explore historical data without volume limitations. -
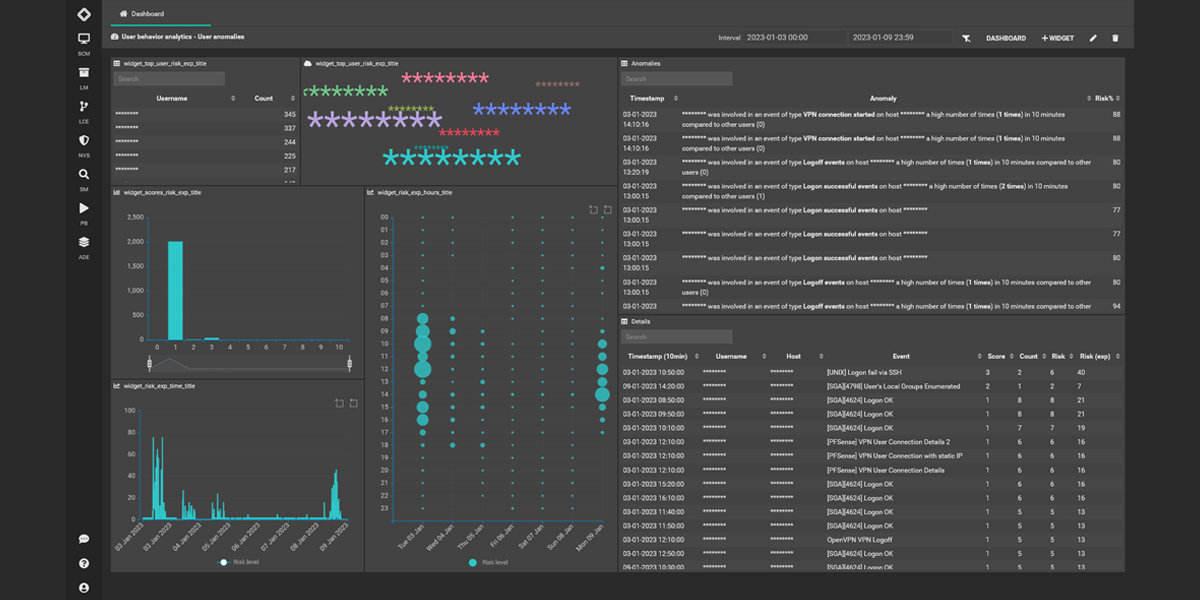
User Behavior Analytics
Detect compromised identities with our User Behavior Analytics (UBA) technology. Our advanced application flags anomalous behavior and quickly identifies compromised user accounts. Protect your business and users with our UBA. -
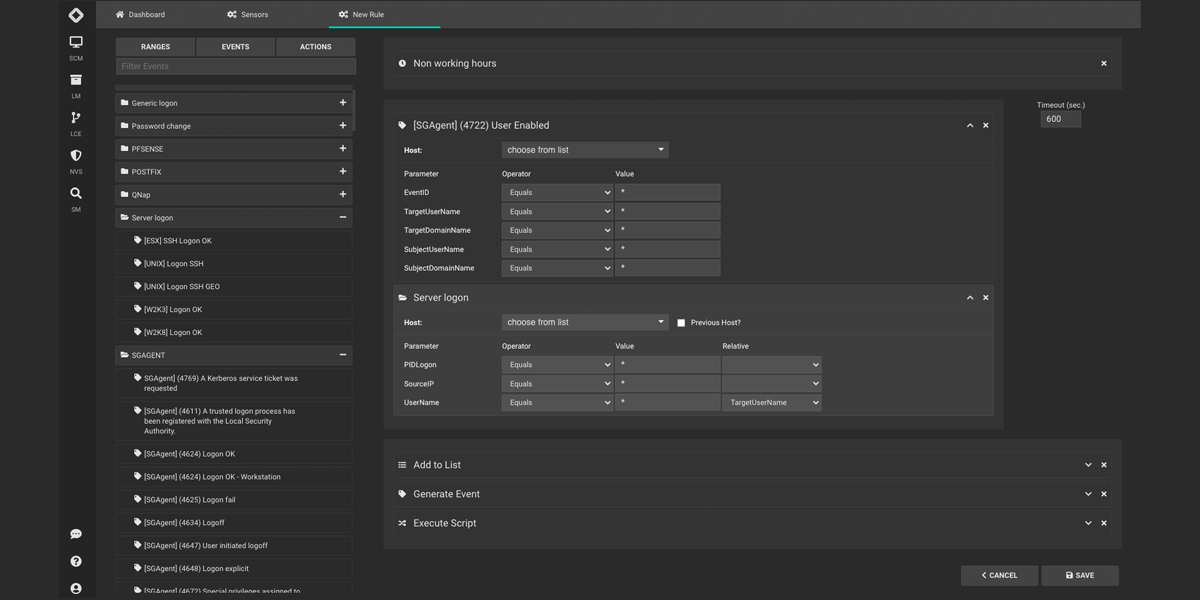
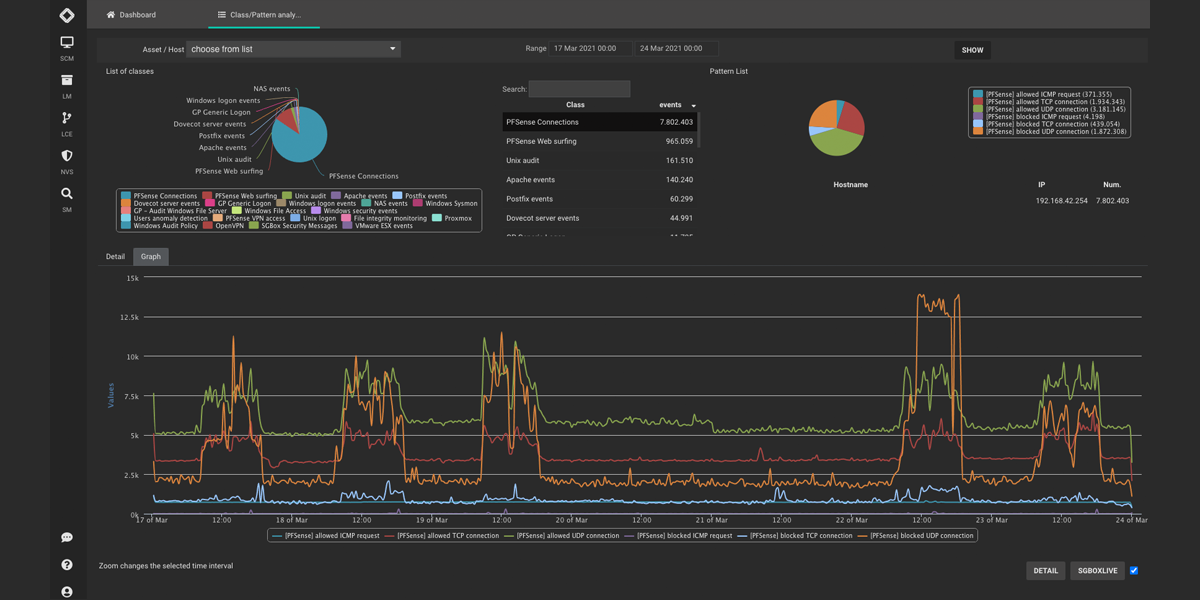
Log Correlation
Protect your network with our Log Correlation Engine. Analyze log data from multiple sources, detect threats with pre-defined rules, and trigger automatic countermeasures. Our intuitive GUI makes it easy to create complex correlation rules in just a few steps. Stay ahead of potential breaches with real-time or historical analysis. Try it now. -
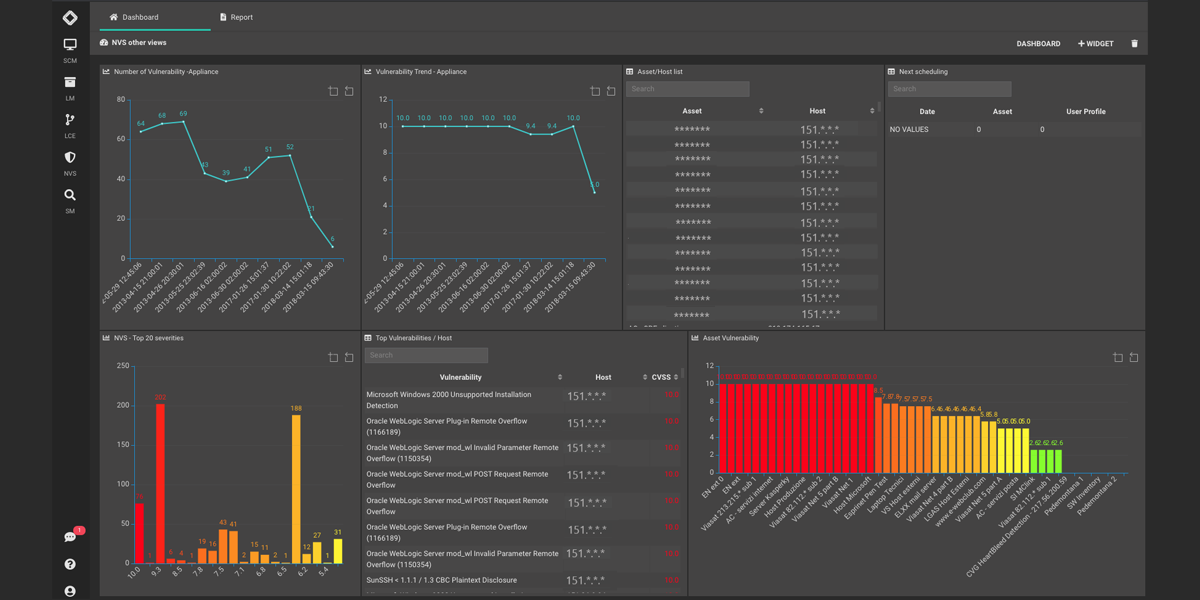
Vulnerability Scanner
Uncover security risks and vulnerabilities with 360CyberTrust's comprehensive strategy for prompt and precise detection of issues in dynamic infrastructures. We provide clear guidance and recommendations to prioritize and address any risks. -
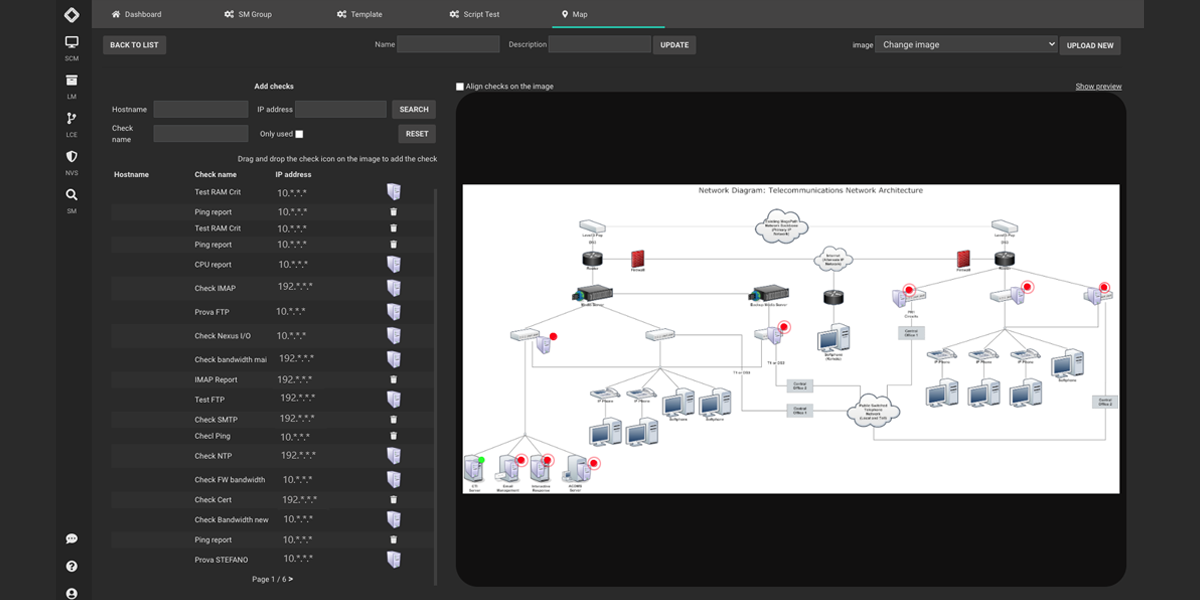
System Monitoring
360CyberTrust monitors network components in real-time to prevent device failure and identify issues quickly, with detailed insights into problematic areas. Integrated with our SIEM platform. -
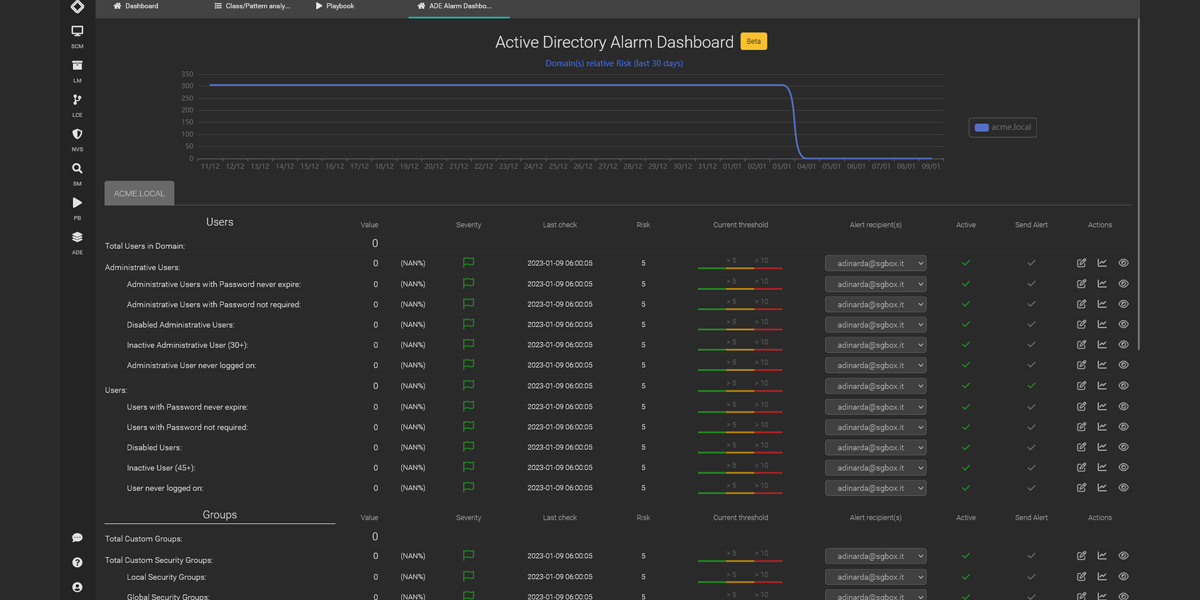
Advanced Windows Auditing
Monitor all endpoints for security, use Windows auditing to track events, SGBox has auditing to ensure compliance, detect threats, and reduce data breach risk. -
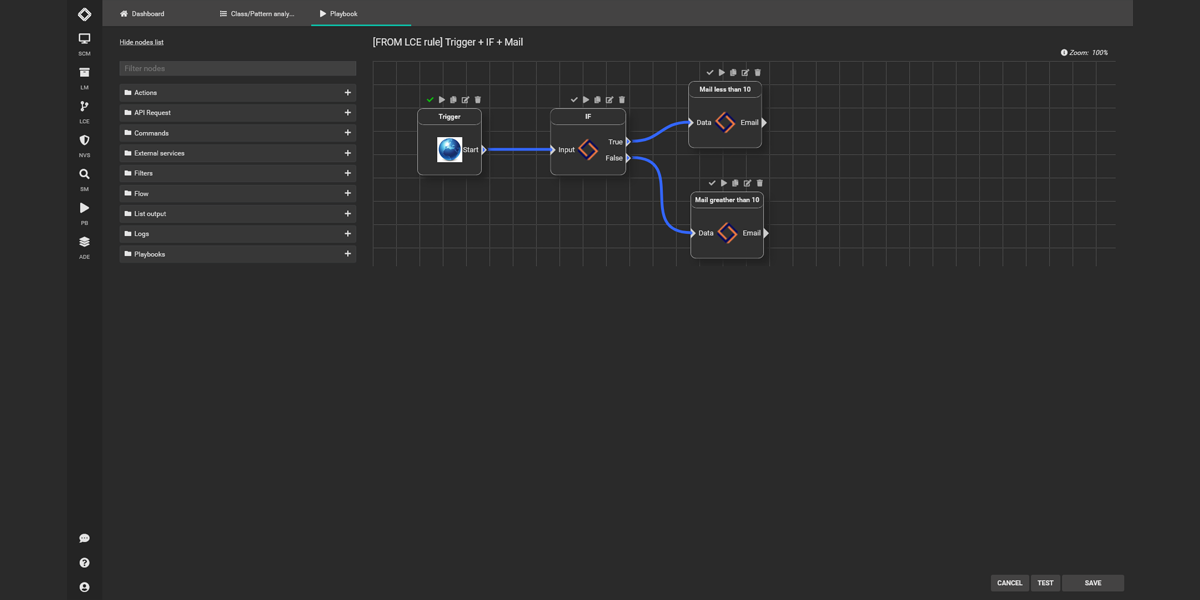
SOAR
Our SOAR module streamlines incident response workflows, automates repetitive tasks, and enhances security operations' efficiency and effectiveness, enabling organizations to quickly and effectively respond to security incidents and protect their critical assets. -

GDPR Gap Analysis
Our Security Information and Event Management (SIEM) application has been specifically designed and developed to support the compliance requirements outlined by the General Data Protection Regulation (GDPR). -
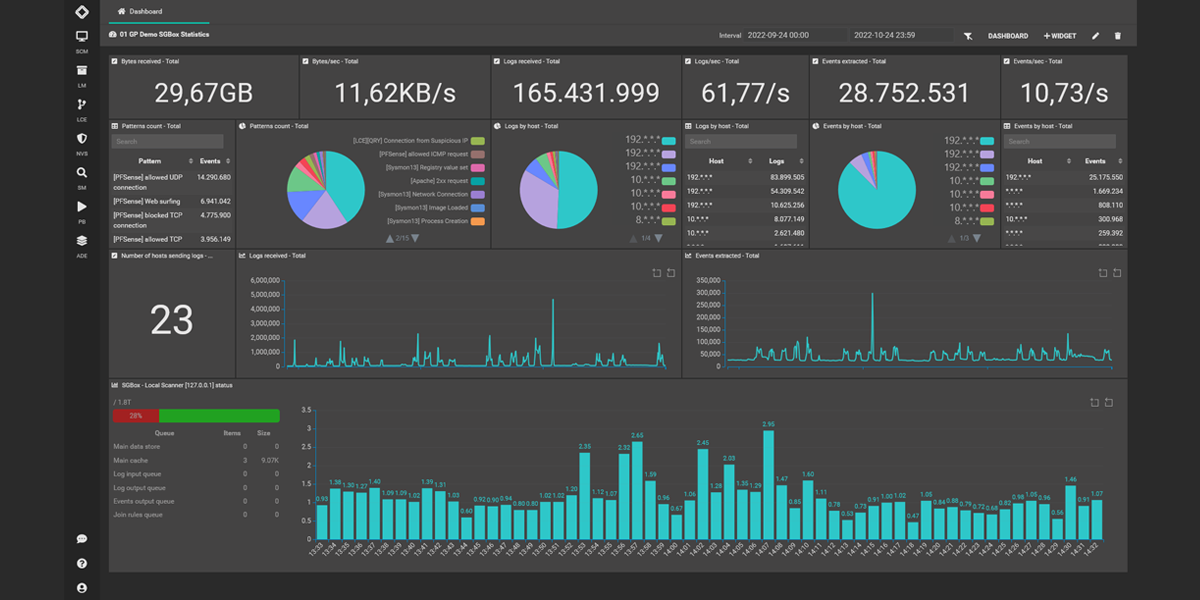
Dashboards and Reports
Deliver a centralized dashboard and comprehensive reports that provide insights into the threat landscape.
-

Log Management
Effortlessly collect, analyze, and visualize data in any format from any device with our user-friendly data management solution. Gain valuable insights in real-time or explore historical data without volume limitations.
-

User Behavior Analytics
Detect compromised identities with our User Behavior Analytics (UBA) technology. Our advanced application flags anomalous behavior and quickly identifies compromised user accounts. Protect your business and users with our UBA.
-

Log Correlation
Protect your network with our Log Correlation Engine. Analyze log data from multiple sources, detect threats with pre-defined rules, and trigger automatic countermeasures. Our intuitive GUI makes it easy to create complex correlation rules in just a few steps. Stay ahead of potential breaches with real-time or historical analysis. Try it now.
-

Vulnerability Scanner
Uncover security risks and vulnerabilities with 360CyberTrust's comprehensive strategy for prompt and precise detection of issues in dynamic infrastructures. We provide clear guidance and recommendations to prioritize and address any risks.
-

System Monitoring
360CyberTrust monitors network components in real-time to prevent device failure and identify issues quickly, with detailed insights into problematic areas. Integrated with our SIEM platform.
-

Advanced Windows Auditing
Monitor all endpoints for security, use Windows auditing to track events, SGBox has auditing to ensure compliance, detect threats, and reduce data breach risk.
-

SOAR
Our SOAR module streamlines incident response workflows, automates repetitive tasks, and enhances security operations' efficiency and effectiveness, enabling organizations to quickly and effectively respond to security incidents and protect their critical assets.
-

GDPR Gap Analysis
Our Security Information and Event Management (SIEM) application has been specifically designed and developed to support the compliance requirements outlined by the General Data Protection Regulation (GDPR).
-

Dashboards and Reports
Deliver a centralized dashboard and comprehensive reports that provide insights into the threat landscape.
Benefits
Benefits

Expert Team
A year-long project can usually be onboard in days from our experts, eliminating the need to train the customer’s staff.
No Physical Resources
A cloud-based system can eliminate the need for physical infrastructures like storage and servers dedicated to the SIEM system.
Always Monitored
Our SIEM Cloud infrastructure and services are always monitored from our experienced team. All problems will be under control.
Improved Security Data
SIEMs aggregate and normalize your security data, improving the potential for it to be analyzed and used in incident response workflows. The SIEM can then store normalized security data for extended analytics and reporting. This not only increases visibility but may also help with compliance.

Increased Visibility
SIEM systems mitigate the risk of threat actors hiding in dark spaces within your network because they are collecting security event data from everywhere in the network. It then works to analyze this data, effectively highlighting those dark spaces.
(Download PDF)
Improved Compliance
SIEM will help you meet demanding compliance requirements. It does this by improving your security posture and helping monitor your organizational environment.


Some other benefits of M-SIEM include:
-
Improved security data:
SIEMs aggregate and normalize your security data, improving the potential for it to be analyzed and used in incident response workflows. The SIEM can then store normalized security data for extended analytics and reporting. This not only increases visibility but may also help with compliance.
-
Increased visibility:
SIEM systems mitigate the risk of threat actors hiding in dark spaces within your network because they are collecting security event data from everywhere in the network. It then works to analyze this data, effectively highlighting those dark spaces.
(Download PDF) -
Improved compliance:
SIEM will help you meet demanding compliance requirements. It does this by improving your security posture and helping monitor your organizational environment.
-
Fewer false positive alerts:
Almost 50% of your security alerts are just “noise”. Machine learning technology can reduce the amount of time your team is spending on false positives, by only highlighting legitimate threats.
-
Dedicated Support:
With SIEM as a service, your account is assigned a dedicated account team to ensure your valued outcomes are always in focus.
Get a free evaluation today
Quick Links
-
About UsAbout Us
-
PartnersPartners
-
Contact UsContact Us
Services
-
SIEM as a service (Cloud)SIEM as a service (Cloud)
-
Managed Security ServicesManaged Security Services
-
Follow UsFollow Us
-
-
Newsletter
-
Privacy PolicyPrivacy Policy
-
Cookie PolicyCookie Policy
-
Terms and ConditionsTerms and Conditions

