Network Vulnerability Scanning
Reduce the Cyber Exposure Gap
Organizations need a modern and comprehensive strategy to quickly and accurately identify vulnerabilities and misconfigurations in their dynamic infrastructures, that delivers clear guidance and recommendations on how to prioritize and remediate any exposures to risk. Our solution understands the cyber exposure of all assets, including vulnerabilities, misconfigurations and other security health indicators.

Vulnerability Management and Advanced Reporting System
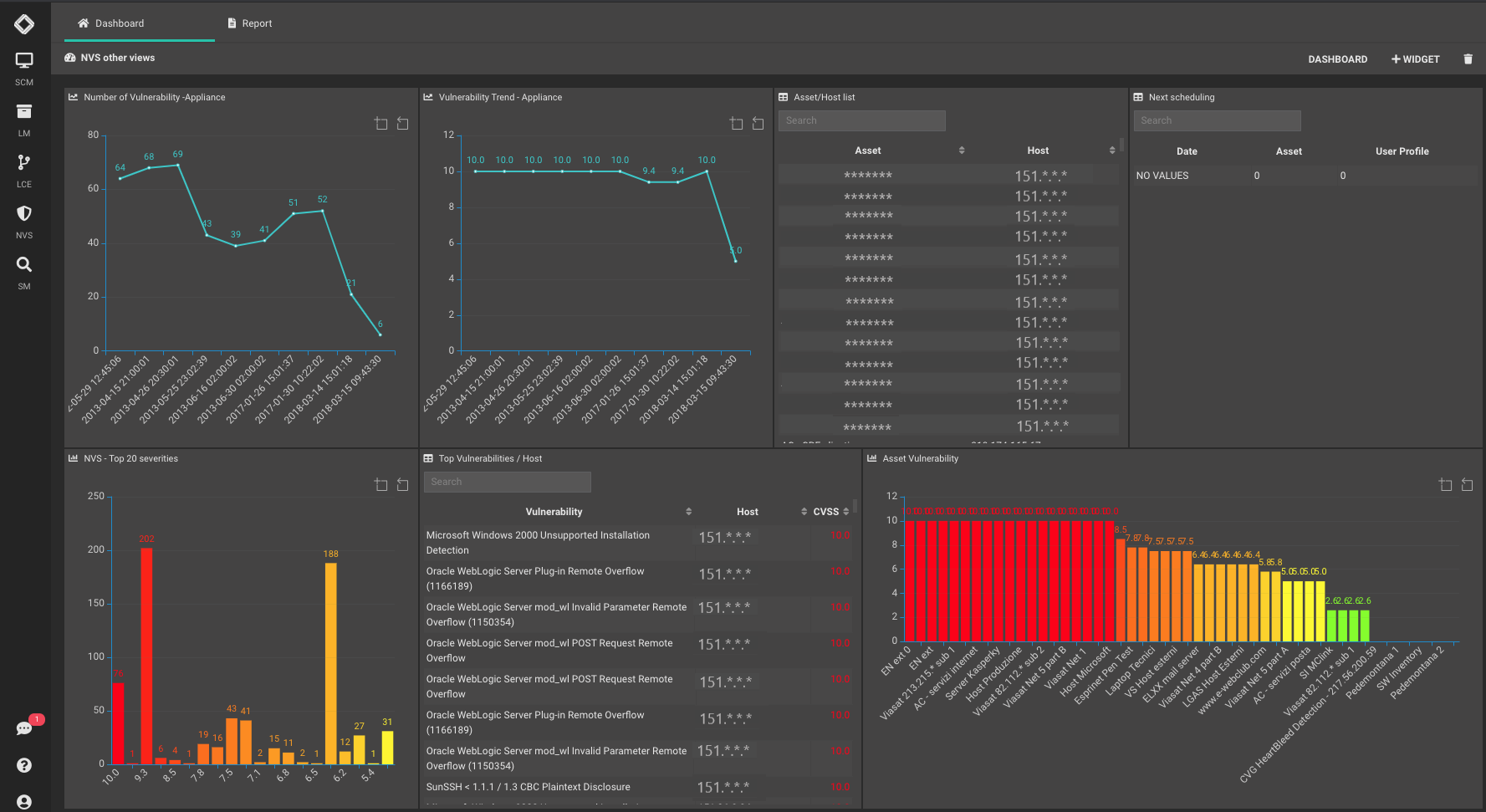
Our platform includes a vulnerability scanning solution to analyze an entity’s security posture. After discovering the network, NVS Module can aggregate pool of assets to define groups and relate custom scanning policies. The scans can be scheduled and every group of assets can be assigned to one or more user who will get automatic reports and alerts. Our NVS adopts the CVSS (Common Vulnerability Scoring System) to rate the scan results for every asset or group. Our NVS Module offers a huge number of reports out-of-the-box, increasing the level of details based of the different recipients. The NVS module can use remote scanning sensors to monitor the vulnerability status of remote or branch offices. The scan engine feeds the Log Correlation Engine using scan statuses and other relevant information to avoid false positives and prioritize the alarms.
-

Vulnerability Prioritization
Our NVS module prioritizes remediation based on asset criticality, threat context and vulnerability severity. Prioritize which exposures to fix first, if at all, and apply the appropriate remediation technique. -

Scans for Compliance
Our NVS is ready to support compliance requirements of major regulations such as GDPR, SAMA Cyber Security Framework, PCIDSS and ISO27001. -

Automate Processes
Live discovery of any digital asset across any computing environment. Leverage different pre-built report template, automate scans and share data with your IT systems. -

Standard Scoring System
NVS uses the CVSS (Common Vulnerability Scoring System), which is an open standard for classifying and scoring the vulnerabilities. This way of attributing scores allows the company to give priority to vulnerabilities and to develop a more effective countermeasure policy. -
Customized Reports
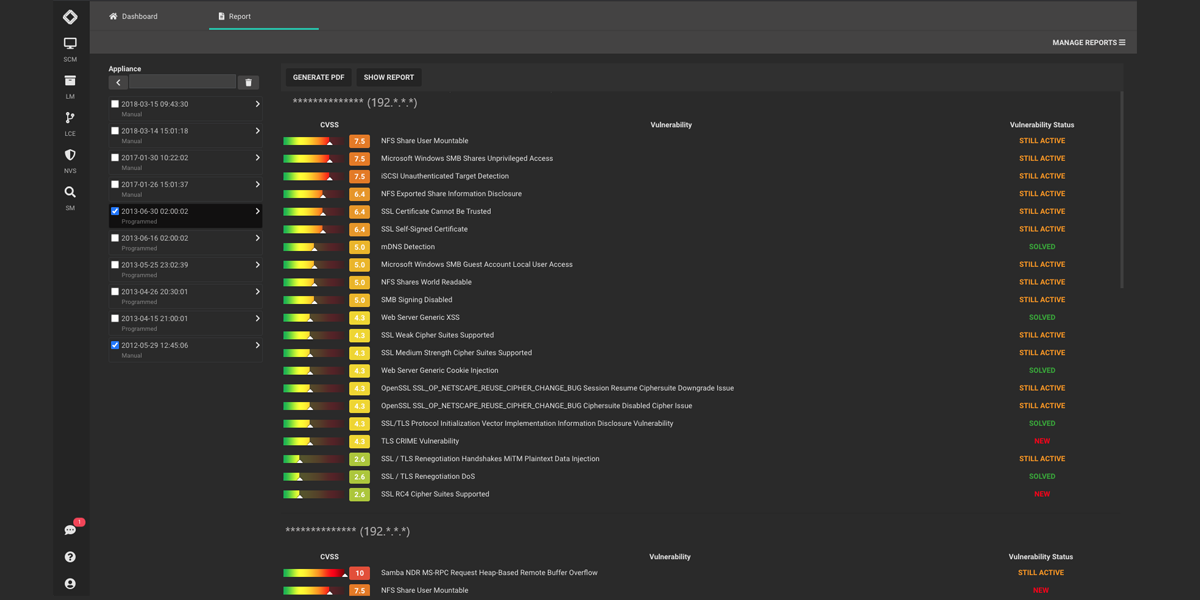
NVS has extensive reporting features which are adapted to the different needs of clients. In fact, tailor made reports can be obtained with different levels of detail for different users in the company such as executives, administrators and auditors. The reports can be freely composed creating templates which summarize the most important information. Incremental and comparative reports are also available.
-

Vulnerability Prioritization
Our NVS module prioritizes remediation based on asset criticality, threat context and vulnerability severity. Prioritize which exposures to fix first, if at all, and apply the appropriate remediation technique. -

Scans for Compliance
Our NVS is ready to support compliance requirements of major regulations such as GDPR, SAMA Cyber Security Framework, PCIDSS and ISO27001. -

Automate Processes
Live discovery of any digital asset across any computing environment. Leverage different pre-built report template, automate scans and share data with your IT systems. -

Standard Scoring System
NVS uses the CVSS (Common Vulnerability Scoring System), which is an open standard for classifying and scoring the vulnerabilities. This way of attributing scores allows the company to give priority to vulnerabilities and to develop a more effective countermeasure policy. -

Customized Reports
NVS has extensive reporting features which are adapted to the different needs of clients. In fact, tailor made reports can be obtained with different levels of detail for different users in the company such as executives, administrators and auditors. The reports can be freely composed creating templates which summarize the most important information. Incremental and comparative reports are also available.
Get a free evaluation today
Contact us now to learn more.
Quick Links
-
About UsAbout Us
-
PartnersPartners
-
Contact UsContact Us
Services
-
SIEM as a service (Cloud)SIEM as a service (Cloud)
-
Managed Security ServicesManaged Security Services
-
Follow UsFollow Us
-
-
Newsletter
Sign up our newsletter for update information, insight and promotion.
-
Privacy PolicyPrivacy Policy
-
Cookie PolicyCookie Policy
-
Terms and ConditionsTerms and Conditions
Copyright © 2023 360 Cyber Trust, All rights reserved