Log Correlation Engine
Correlation, Alerts And Automated Response

Visibility of Dynamic Multi-Step Events
Quickly and Confidently
-
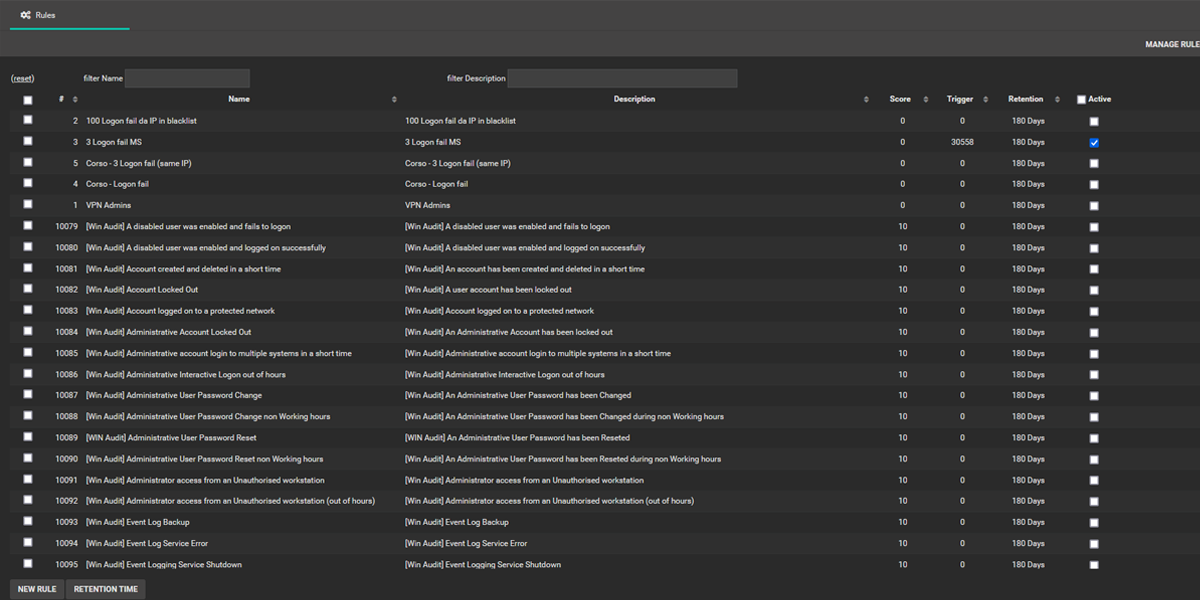
Predefined Rules Set
It is possible to choose correlation rules from many predefined templates, constantly updated and guaranteed by the experience of our Security Engineers.
-

File Integrity Monitoring
Monitor file activities to protect sensitive information from theft, loss and malware. Check and view details or changes made to files and folders identifying an advanced persistent threat attack.
-

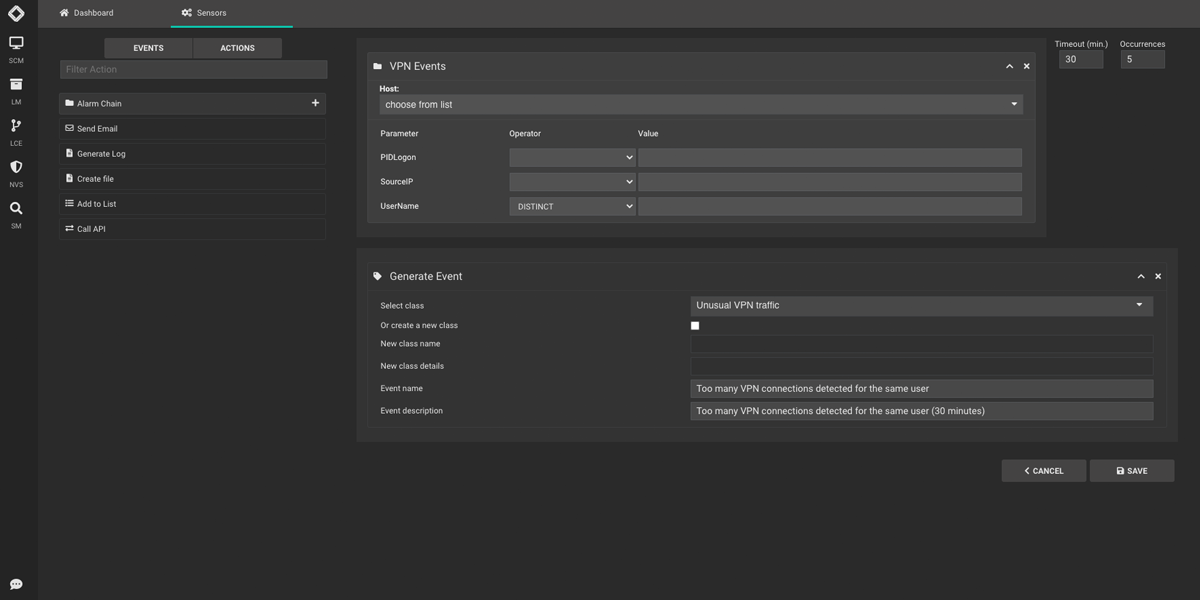
Automated Response
The Log Correlation Engine can engage automated response in case of threats by launching scripts or interacting with security components via API or APPs to mitigate threats.
-
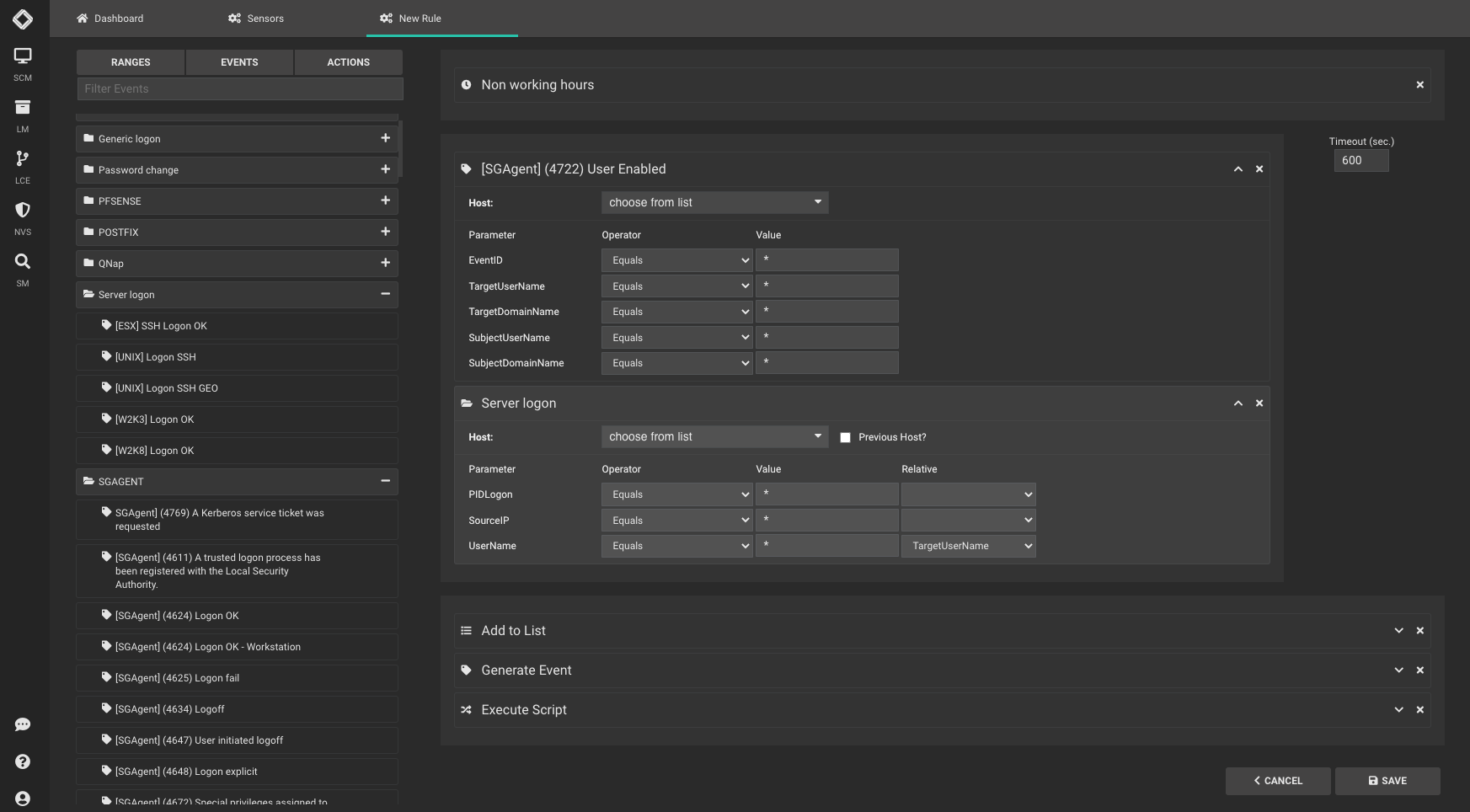
Easy To Use
Create your own rules in few steps by drag and drop: time-range, events and actions
-

Predefined Rules Set
It is possible to choose correlation rules from many predefined templates, constantly updated and guaranteed by the experience of our Security Engineers.
-

File Integrity Monitoring
Monitor file activities to protect sensitive information from theft, loss and malware. Check and view details or changes made to files and folders identifying an advanced persistent threat attack.
-

Automated Response
The Log Correlation Engine can engage automated response in case of threats by launching scripts or interacting with security components via API or APPs to mitigate threats.
-

Easy To Use
Create your own rules in few steps by drag and drop: time-range, events and actions
Open Platform
Integrates with existing infrastructure components, enables custom workflows and interaction with third party applications
Forensic Analysis
This discovery offers a full spectrum of information system-focused investigative capabilities base on manual research
Get a free evaluation today
Quick Links
-
About UsAbout Us
-
PartnersPartners
-
Contact UsContact Us
Services
-
SIEM as a service (Cloud)SIEM as a service (Cloud)
-
Managed Security ServicesManaged Security Services
-
Follow UsFollow Us
-
-
Newsletter
-
Privacy PolicyPrivacy Policy
-
Cookie PolicyCookie Policy
-
Terms and ConditionsTerms and Conditions